IP Address, OSI Layer
Fundamental Networking Concepts
IP Addressing & Subnetting
Transition between IPv4 and IPv6
Based on my research regarding these two IP. IPv6 is intended to be IPv4 successor. there is key factor why IPv4 still can be used until now
- NAT (Network Address Translation): NAT allows multiple devices on a private network to share a single public IP address, effectively extending the lifespan of IPv4. It's a band-aid solution, but widely deployed.
- Backward Compatibility and Transition Challenges: Transitioning from IPv4 to IPv6 isn't as simple as flipping a switch. It requires significant infrastructure upgrades and software changes. Many legacy systems and applications were designed for IPv4. Ensuring backward compatibility during the transition is complex.
- Lack of Immediate, Tangible Benefits for End Users: While IPv6 offers significant advantages (vastly larger address space, improved security, better routing efficiency), these benefits aren't always immediately apparent to end users, especially if their current IPv4 connectivity works.
- Inertia and Lack of Urgency: Some organizations and ISPs have been slow to adopt IPv6 due to the costs and complexity involved, especially when IPv4-based solutions (with NAT) seem to suffice for now.
OSI Model (Open Systems Interconnection Model)
Definition
The OSI model is a conceptual framework that divides the complex process of network communication into seven distinct but interconnected layers. Think of it as a layered cake, where each layer represents a specific stage in the data transmission process.
The Seven Layers of the OSI Model:
Each layer has its own specific functions and protocols. Data travels down from the application layer to the physical layer on the sending device, then back up from the physical layer to the application layer on the receiving device.
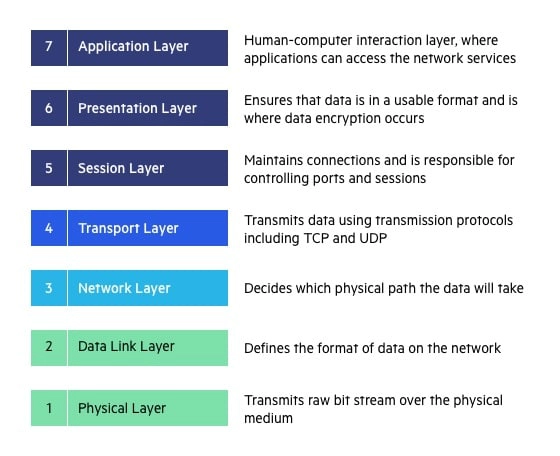
Layer 7: Application Layer
Purpose: Provides services to the applications that users interact with (e.g., web browsers, email clients).
Key Protocols:
- HTTP (Hypertext Transfer Protocol): For accessing websites.
- HTTPS (HTTP Secure): The secure version of HTTP.
- SMTP (Simple Mail Transfer Protocol): For sending emails.
- FTP (File Transfer Protocol): For transferring files.
- DNS (Domain Name System): For translating domain names to IP addresses.
Layer 6: Presentation Layer
Purpose: Ensures that data is presented in a format that the receiving application can understand.
Key Functions:
- Data Formatting: Converts data between different formats (e.g., ASCII, Unicode).
- Encryption/Decryption: Handles encryption and decryption for secure communication.
- Data Compression: Compresses and decompresses data to optimize transmission efficiency.
Layer 5: Session Layer
Purpose: Establishes, manages, and terminates communication sessions between applications.
Key Functions:
- Session Establishment/Termination: Sets up and tears down communication channels between applications.
- Synchronization: Adds checkpoints to data streams to allow for resynchronization if a connection is interrupted.
Layer 4: Transport Layer
Purpose: Provides reliable and efficient data transfer between applications on different hosts.
Key Protocols:
- TCP (Transmission Control Protocol): Connection-oriented, reliable, provides error checking and flow control (used by HTTP, FTP, SSH).
- UDP (User Datagram Protocol): Connectionless, faster but less reliable than TCP (used for DNS, video streaming, online gaming).
Layer 3: Network Layer
Purpose: Handles addressing and routing of data packets across networks.
Key Protocols:
- IP (Internet Protocol): Provides logical addressing (IP addresses) for devices on a network.
- IPv4: The older, 32-bit version of IP.
- IPv6: The newer, 128-bit version of IP.
- ICMP (Internet Control Message Protocol): Used for error reporting and network diagnostics (e.g., ping).
Layer 2: Data Link Layer
Purpose: Provides node-to-node data transfer (within the same network segment).
Key Functions:
- Physical Addressing: Uses MAC (Media Access Control) addresses to identify devices on a local network.
- Error Detection and Correction: Detects and corrects errors that might occur during transmission.
- Flow Control: Manages the rate of data flow between devices to prevent congestion.
- Ethernet: The most common standard for local area networks (LANs). It defines how data is formatted and transmitted on a physical network segment.
- Wi-Fi (Wireless Fidelity): A wireless networking standard that uses radio waves to provide network connectivity. It operates at the Data Link Layer to handle addressing (MAC addresses) and error detection within a Wi-Fi network.
Layer 1:Physical Layer
Purpose: Defines the physical characteristics of the network, transmitting raw bit streams over a physical medium.
Key Concepts:
- Cabling: Copper (e.g., Ethernet), fiber optic.
- Signaling: Electrical or optical signals that represent the data bits.
- Physical Connectors: RJ-45 (Ethernet), SC/LC (fiber optic).
OSI Example
Database (e.g., MySQL, PostgreSQL)
Application Layer (Layer 7): The database server itself, accepting SQL queries and returning results. Transport Layer (Layer 4): Communication between the database client (your application) and the database server often uses TCP.
Cache (e.g., Redis, Memcached)
Application Layer (Layer 7): The cache server, providing fast data retrieval. Transport Layer (Layer 4): Communication with the cache server often uses TCP or UDP.
CDN (Content Delivery Network)
Application Layer (Layer 7): CDN edge servers cache content (images, videos) closer to users. Transport Layer (Layer 4): Communication between users and CDN edge servers often uses HTTP (over TCP).
Message Brokers (e.g., RabbitMQ, Kafka, ActiveMQ)
Application Layer (Layer 7): Applications interact with the message broker through APIs to publish and consume messages. Transport Layer (Layer 4): Communication between producers, consumers, and the broker often uses TCP for reliable message delivery.
API Gateways
Application Layer (Layer 7): Act as reverse proxies, handling requests from clients, routing them to appropriate backend services, and enforcing security policies.